wodSSHTunnel ActiveX component
SSH Tunnel ActiveX, SSH component

Pricing per developer
License provides one year of free updates and unlimited lifetime technical support. Each developer must have his own design-time license.
 General information
General information
The wodSSHTunnel component is a client/server component that will add secure tunneling capabilities to your applications and is based on the SSH protocol. According to your rules and definitions, it will accept local connections, encrypt and forward data to the SSH server where it will then be decrypted and sent to the destination host. An SSH server is required for this component to work - encryption will take place between the local computer (running wodSSHTunnel) and the SSH server of your choice.
It will work on both ends - it can accept local connections and forward them to the server or it can facilitate connections to local services when notification of a 'remote port forwarding' request is received from an SSH server.
wodSSHTunnel also implements a SOCKS4(a)/SOCKS5 proxy - so you can leave it up to each application to decide its destination dynamically.
 How does it affect your network connections?
How does it affect your network connections?
Instead of using direct connections to the server, through the insecure Internet,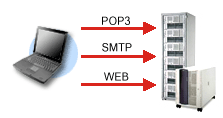
you would connect to your SSH server using an encrypted connection and the SSH server would connect to the services that you require. Usually, these services will reside on the same machine as the SSH server or will be inside a protected network.
Not only will it secure your connections, it will also allow you to create a VPN to your services.
 How does it work?
How does it work?
You setup any number of Channels - these are objects that will keep information about a specific port forwarding request. For example, you can create a Channel that will listen on local port 80 and forward all requests to an SSH server on its port 80. After you Start that channel, you can connect to http://localhost using your web browser and you will see the web page served up by the web server that is running on the same computer as the SSH server. Neat, isn't it?
After a Channel is created and started, it will accept Users. Each channel stores a collection of users that are connected to it. When a new User tries to connect to the channel, you will receive an event in which you can decide whether to allow or deny the user permission to use the secure channel. If you allow a user to connect and use a channel, everything else is handled by wodSSHTunnel.
 Where would you use it?
Where would you use it?
If you are looking for a tunneling component, you probably already have an idea where you would use it. But if you don't have any idea, here is a suggestion: you can encrypt your email transfers with a wodSSHTunnel. You do this by setting up a channel to listen on port 110 (for the POP3 protocol) and point it to the server on port 110. Once this is in place, you can use your email client to connect to localhost on port 110 and all of your email transfers will be encrypted. This is a great tool when you are reading your email from public computers or Internet cafes.
You can also encrypt the SMTP protocol this way. Not only is it secure but you can also bypass relay checking on your SMTP server. When you send email through the tunnel in this way, the SMTP server sees mail as coming from localhost (on its side!) and will allow relays. This is not a security flaw, because you have already authenticated with the server using the SSH protocol.
 Programming considerations
Programming considerations
wodSSHTunnel comes in three flavors:
- as an in-process COM object (or ActiveX DLL)
- as an out-of-process COM object (or ActiveX EXE)
- as an ActiveX custom control (or OCX)
You can drag&drop the as ActiveX control onto your form and you can set up basic properties (and even define channels!) using its property pages.
 Licensing
Licensing
As is usual with WeOnlyDo! products, wodSSHTunnel is a royalty free component. You have the right to distribute its binaries (wodTunnel.dll, wodTunnel.exe, wodTunnel.ocx, wodKeys.dll) with your application, free of charge. You only need to purchase separate licenses for each developer on your project. Under no circumstances are you entitled to sell, give away or change the component's source code - this still belongs to WeOnlyDo! Software.
 Environments
Environments
wodSSHTunnel can be used in many environments, wherever it makes sense to run server-type applications. However, if you try to use it from within ASP it probably won't work.
 Additional notes
Additional notes
wodKeys component is included in our setup package free of charge. It can be used for private key management - to Generate new keys, Load/Save keys, obtain public keys etc. The helpfile can be found here.
In SSH1 you cannot use remote port forwarding due to specific limitations of this protocol.

















